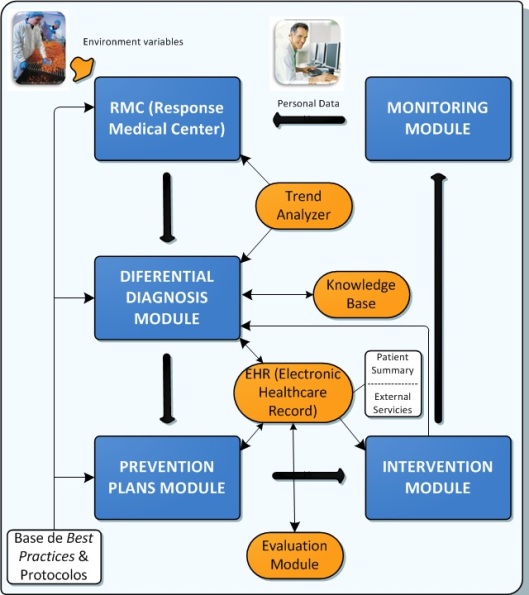
Next figure presents the architecture for the
“Health Continuous Vigilance System” developed inside
the FASyS project. This system is based on five main parts:
Monitoring Module; Response Medical
Center; Differential Diagnosis Module;
Prevention Plans Module; and Intervention
Module. Each of these parts can be influenced by a number of external
variables and parameters such as the Electronic Healthcare Record
(EHR).
Given the big amount of generated information in
this model, it is necessary to process all the collected data, since such amount
of information would not be easily understandable by health professionals.
Services and intelligent devices that have been generated will provide a
classification of the monitored data. Some data will be set inside a normal
range, and others will be out of the settled limits, generating alarms due to
this. Furthermore, this classification will help the doctor to organize and
evaluate all workers’ data and at the same time it will be able to act more
precisely against a particular diagnostic.
Therefore, the Monitoring Module
is where is stored all the personal information gathered by the system about the
worker himself. All these personal data, obtained from the monitoring, are
complemented and improved by variables from several sensors in the factory
(collecting temperature or humidity, that is, particular characteristics from
the workplaces at which the worker can stay during a work journey), that are
joined all together in the Response Medical Center (RMC). The
RMC allows to filter and organize the population depending on the changeable
rules and on the user role. So, it is in this module where the first amount of
data is collected, creating, as a result, personalized records of the workers
and establishing alerts which make easier the task of health professionals.
The information stored in the previous module is
not enough to make a complete diagnosis. So, data from other sources are needed,
such as:
- Data from a medical base of knowledge (it contains relations among diseases, risks, medical tests, medical recommendations, etc).
- Personal data from the health system, which include the previous medical history and it is known as Electronic Healthcare Record (EHR).
- Trend analyzer data. This system is in charge of detecting how some parameters of a person are changing during the pass of time. These parameters can be added to the absolute values in order to get a more complete evaluation of the person.
- Evaluation module results. It can be defined as a “photograph of the person” in a particular moment, with no need to detect a problem.
These four mentioned sources are the subsystems
which provide important information to the main blocks. To manage all this
information, a Differential Diagnosis Module has been developed
(Dr. House influence gets far). This module, through intelligent systems, helps
in making decision to health professionals.
The next step is to reach the Prevention
Plans Module, where it is defined how to act. The plans to be taken can
be of two types: in one hand a medical diagnosis and in the other hand a
technical diagnosis, for instance a redesign of the workplace. It is important
to remark that these actions are not exclusive. According to this, different
levels of action can be established; that is, from very complex levels to more
simple levels such as, for example, reminder panels. In addition, the prevention
actions carried out in this module can be conducted at three level:
- At the first level, the system reacts automatically. When one of the collected data reaches a condition that the professional wants to be controlled, there is an automatic reaction. This associated reaction can be the activation of an alarm, a protocol in a situation of risk, etc. These automatic reactions are achieved using ECA rules (i.e. Event-Condition-Action rules).
- At the second level, health professionals receive the alerts and then they react in consequence, acting on individual workers. The reaction of professionals can be the assignation of a prevention plan developed before, or the assignation of a prevention plan modified for the worker situation in particular. These ways that define the processes are called workflows. (Note: these workflows will be treated in a more detailed way in next posts).
- The third level is in charge of providing knowledge for the other two levels, improving the protocols, adapting them to new situations and personalizing the recommendations. Innovative intelligent tools are used to manage it.
Finally, the Intervention Module
is responsible for performing the particular actuation selected for the
problem in question.
How it can be seen in the above figure, the
“Health Continuous Vigilance System” is cyclic and works in a
continuous fed-back learning way, therefore, after the Intervention Module, it
starts again from the Monitoring Module.
Another important aspect to take into account is
the personal data privacy. As a consequence of this, only a few people will have
access to the EHR (Electronic Healthcare Record), to the personal variables, and
to the personal diagnosis.
Finally, to complete a previous post, it should be emphasized that NOMHAD application is used in the
Response Medical Center Module; in fact it is the main tool of this
module.
A next post will be dedicated to complete the vision of Tissat collaboration on FASyS Project, and we’ll focus on workflows used for prevention protocol implementation, as well as in the use of a “choreographer” to interconnect services, and in the management of PHR (Personal Health Record).
A next post will be dedicated to complete the vision of Tissat collaboration on FASyS Project, and we’ll focus on workflows used for prevention protocol implementation, as well as in the use of a “choreographer” to interconnect services, and in the management of PHR (Personal Health Record).